Endpoint Privilege Manager
Remove local admin rights, enforce least privilege, and implement foundational endpoint security controls across all Windows, macOS and Linux endpoints from hybrid to cloud environments.

Endpoint Privilege Manager
Implement flexible and intuitive policy-based endpoint privilege management
Manage Privileges on Windows, macOS and Linux
Reduce your attack surface by removing local admin rights
Endpoint Privilege Manager helps remove local admin rights while improving user experience and optimizing IT operations.
Flexible policy-based management simplifies privilege orchestration and allows controlled Just-In-Time maintenance sessions.
Enforce Least Privilege
Comprehensive conditional policy-based application control helps you create scenarios for every user group, from HR to DevOps. Application context, parameters and attributes are considered to allow or block certain script, application or operation.
Defend Against Ransomware
Ransomware can be tricky so we continuously test Endpoint Privilege Manager against new strains of ransomware. And so far, with over 3,000,000 different samples thrown at it, Endpoint Privilege Manager has proven to be 100% effective against this attack vector.

Boost Visibility with Policy Audit
Endpoint Privilege Manager’s Policy Audit capabilities enable you to create audit trails to track and analyze privilege elevation attempts. The rich reporting engine helps you maintain visibility and control over your endpoints.

Stop Credential Theft
Credential theft enables attacker to move laterally and is a major part of every breach.
Endpoint Privilege Manager defends credentials and credential stores and helps detect attacks early with credential lures placed in attackers’ pathways.

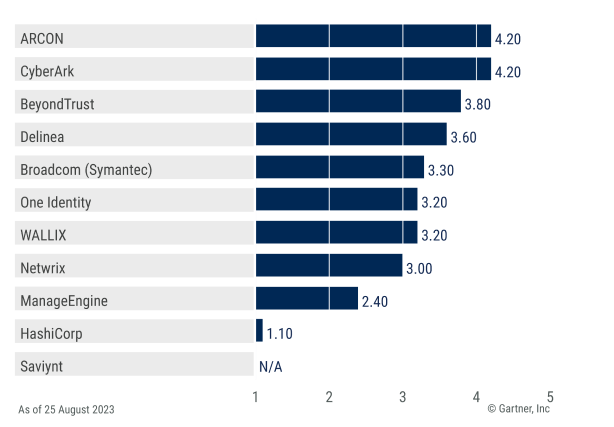
CyberArk scored highest in the Windows PEDM use case in the 2023 Gartner Critical Capabilities for PAM.
Foundational endpoint security
Endpoint-originating attacks can be devastating, ranging from disruption to extortion. But increased investment in traditional endpoint security has failed to reduce the number of successful attacks.
Endpoint Privilege Manager, a critical and foundational endpoint control addresses the underlying weaknesses of endpoint defenses against a privileged attacker and helps enterprises defend against these attacks.
Defend against attacks
Render vulnerabilities unexploitable by removing local admin rights.
Drive operational efficiencies
Simplify IT workflows and harden endpoints without impacting productivity.
Enable the digital business
Align security to business goals and encourage user independence and flexibility.
Satisfy audit and compliance
Address specific regulatory requirements and create audit trail for privileged actions.

“I have deployed CyberArk in companies as small as 150 users, all the way up to Quanta with 16,000 endpoints and numerous individual accounts. Each time, my approach was identical. The rollout with CyberArk works no matter the size of the company.”
Richard Breaux, Senior Manager, IT Security, Quanta Services

“Because of the policies that we created using CyberArk – by role, department and function – our rules are now tightly aligned to the overall company goals. Now the right people get the right access when they need it.”
Aman Sood, General Manager of IT Infrastructure, Icertis

“The fact that we’re rotating passwords and preventing system
breaks has been a huge benefit for our development teams. The ability to pull usernames and credentials at the end of development saves them a lot of time.”
Adam Powers, Lead Info Security Engineering Manager, TIAA

“We fell in love with the solution. Not only did it solve the issues we were facing around local administrator privileges, but it also had the granular controls that empower users to make administrative actions with the necessary guardrails.”
Director of Client Services, Major US Research Hospital

“It doesn’t mean we won’t get hit again, but because of CyberArk, we’re now properly equipped and very aware of what’s going on. I really feel that we are in a much better place than we were prior to the ransomware attack.”
Director of Identity & Access Management, Global Holding Company
Better together
Defend against privilege abuse, exploits and ransomware with the broad out-of-the-box integration support and a flexible API. As part of our extensible Identity Security Platform, Endpoint Privilege Manager simplifies deployment and streamlines IT operations.
Microsoft Azure AD SAML
Leverage Azure AD SAML to authenticate administrative users
Secure Amazon WorkSpaces
Enforce least privilege on Amazon WorkSpaces Desktop-as-a-Service (DaaS) instances
Automate JIT Requests With ServiceNow
Streamline and automate Just-In-Time (JIT) session requests servicing
CyberArk Secure Desktop
Learn how CyberArk identity solutions can help defend against cyber attacks
Comprehensive and scalable SAAS architecture
CyberArk is experienced in delivering SaaS solutions, enhancing security, cost effectiveness, scalability, continued evolution, simplicity and flexibility.
Explore
additional
resources
Get a 30-day trial
Strengthen security
Reduce risk
Increase productivity
Work safely from anywhere

Sign up now
Every submission is subject to review. Registrants must provide business contact information to be eligible. To better help trial participants, please provide which use cases that are of interest to validate in the “Goals for Trial” field.