User Behavior Analytics
A smart, AI-powered engine to collect, analyze, and visualize user behavior insights in real-time.

User Behavior Analytics
Intelligent access decisions
A User Behavior Analytics engine embedded in CyberArk’s Workforce Identity solutions.
Visualize risk
Use interactive dashboards to drill into the context behind security events and pinpoint root causes.
Uncover threats
Eliminate manual review of log data and use AI to identify patterns of risky access conditions.
Demonstrate compliance
Configure dashboards and in-depth reports to report on access-related events and activities.
Know your users inside, and out
Use third-party data as a threat vector in your risk calculation models.
- Extensible sensor-based architecture to ingest third-party log data
- Dynamically adjust risk profiles for individual users
- Use events captured by Palo Alto Networks Cortex Data Lake

Put security first without putting productivity second
Ensure secure access, without slowing down users.
Develop dashboards
Enhance visibility across access points to ensure that policy is working as expected with dashboards that tally alerts and visualize trends.
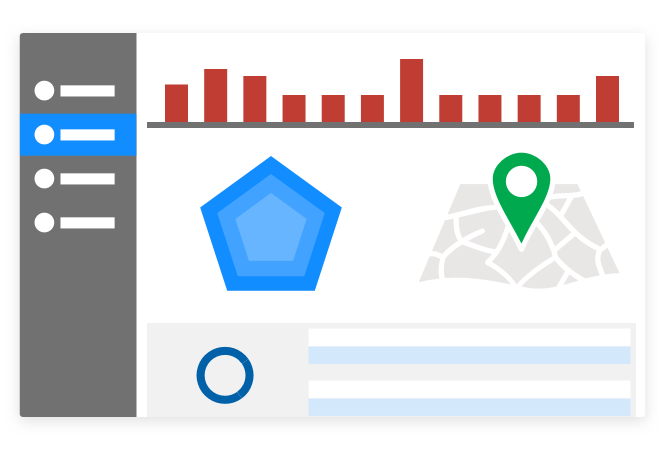
Prioritize risks
Prioritize alerts based on risk and easily identify compromised accounts to remediate suspicious activity and stop threats.
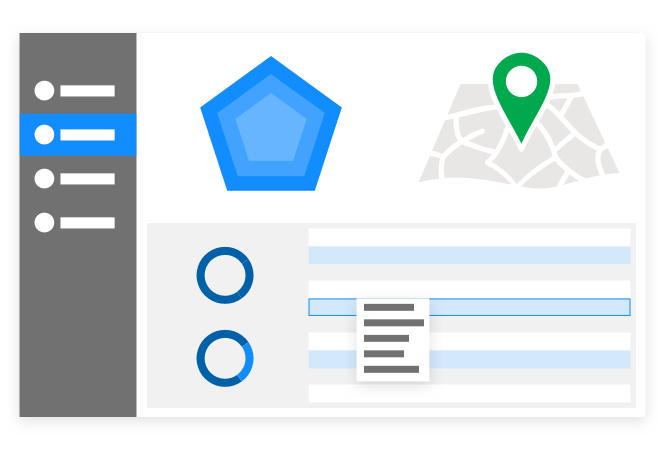
Monitor access
Interactive reports make it easy to identify specific accounts that have been compromised, or why a user was prompted for MFA, blocked or allowed access.
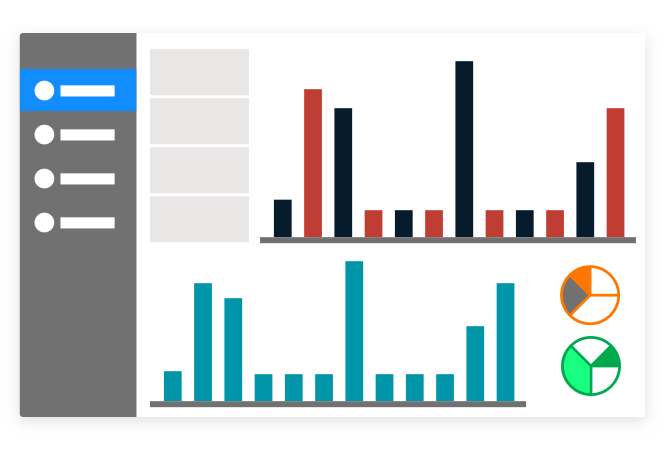
Investigate events
Interactively pivot and visualize datasets, isolate specific access events and examine event details including time, location, and device from which the request originated.
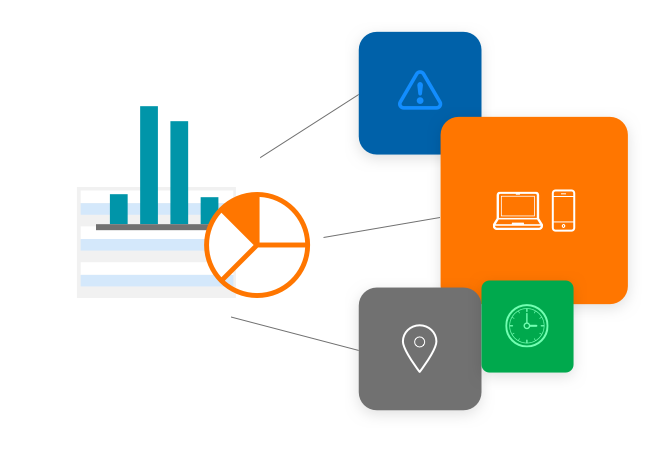
Automate alerts
Send access event details to third-party applications that accept incoming webhooks. For example, set up a webhook to trigger a Slack notification to your Security Team about a high-risk access request.


“The CyberArk Identity Security Platform is a great tool for providing simple and secure access to our staff. By removing the burden of creating and remembering passwords and offering seamless, one-click access, we are improving productivity and enhancing our security posture.”
John Vincent, Director of Technology, Chico Unified School District

"CyberArk has been the best vendor I have worked with in my 20+ year IT career. CyberArk delivers great products that lead the industry in managing privileged access."
IT Security Manager, Security and Risk Management

"With CyberArk, we are confident that we have implemented technology that will work with us as our business grows and develops."
Jean-Pierre Blanc, Bouygues Telecom

"This isn’t just a compliance check-box exercise, we’re actively designing and aligning policies to cybersecurity best practices to strengthen our overall security posture and align internal teams."
Joel Harris, Manager

"CyberArk gave us the visibility and granular control needed to implement both least privilege and ‘default deny’ application control with minimal disruption to the organization."
Ken Brown, CISO

"With RPA and Cloud migrations, credentials are becoming more and more spread out away from 'normal' controls. CyberArk can spread out to cover all of the scenarios in a standard way."
Information Security Consultant, Enterprise Cybersecurity Solutions Technologies
Identity security that knows you but doesn’t slow you
Explore all the ways CyberArk gives you peace of mind to move fearlessly forward.
Get a 30-day trial
AI engine behind CyberArk Workforce Identity solutions
Real-time security analytics and context-aware risk assessment
Suspicious behavior alerts
Rich tools and dashboards